
Signs you’ve been hacked
- You’ve been logged out of your account.
- You find logins from devices or locations that you don’t recognize in your account activity.
- You received emails or text messages for login attempts, password resets, or 2FA codes that you didn’t request.
- You’ve received security emails from the service about account activity you don’t recognize.
- Your sent folder has emails that you didn’t send.
- There are purchases in your account that you don’t recognize or you see unauthorized charges in your linked payment method.
- The data in your account is altered or missing.
- Your contacts are receiving strange emails or messages from you in email or social media accounts.
- There are posts on your social media you didn’t make.
- There are unusual changes in your account settings like updated recovery information.
- Your emails are automatically getting forwarded to an email address you don’t recognize.
- New apps or extensions are connected to your account that you didn’t authorize.
- Your account has been locked due to suspicious activity.
- You cannot log in to your account.
If you think you’ve been hacked, most popular online services have tools in place you can use to check for unusual activity and take further action if required.
Securing your Google account is important because it’s linked to many websites and apps out there and can be used to hack into them as well.
- If you think someone can access your Google account, go to your Gmail account and scroll down to the bottom.
- Click on ‘Details’ below ‘Last account activity’.
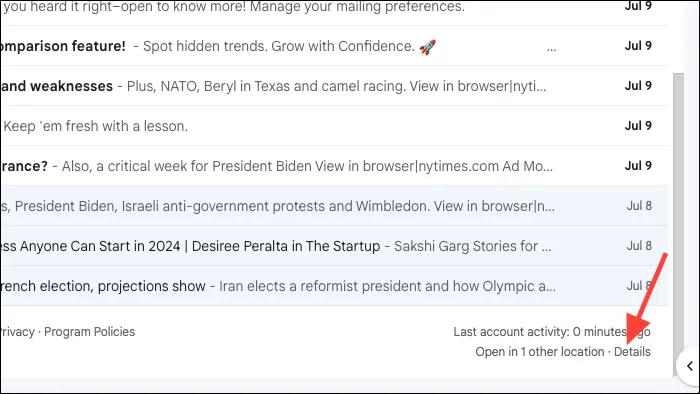
- You’ll be able to see all the places where your account is active. Click on ‘Show details’ to view more information about it. If you don’t recognize a location, click on the ‘Security Checkup’ link to investigate it further.
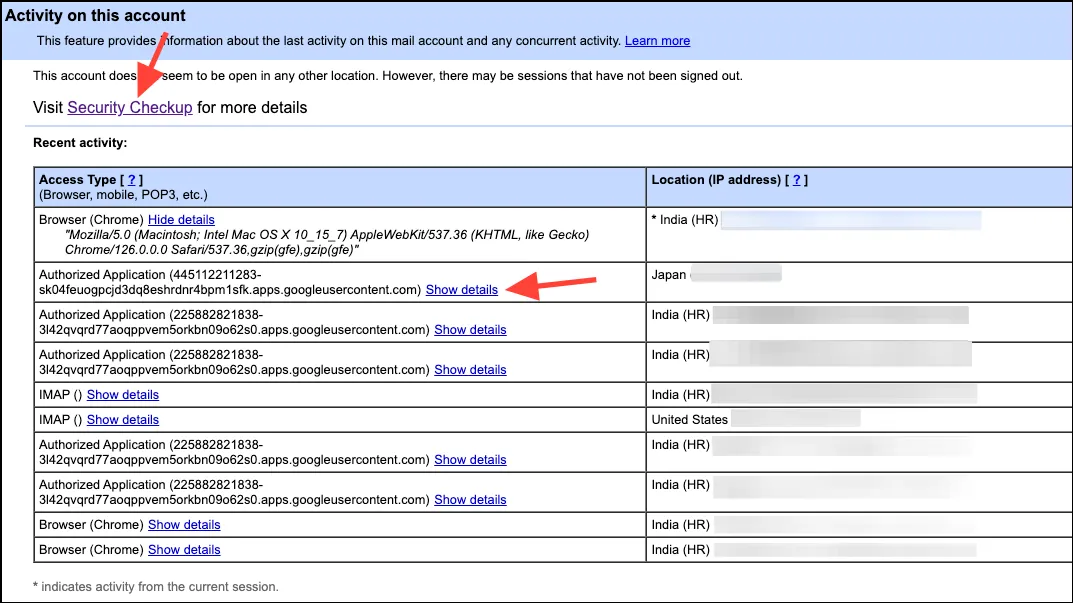
- Here, you can see the devices that have access to your account and remove any device you don’t recognize or use anymore.
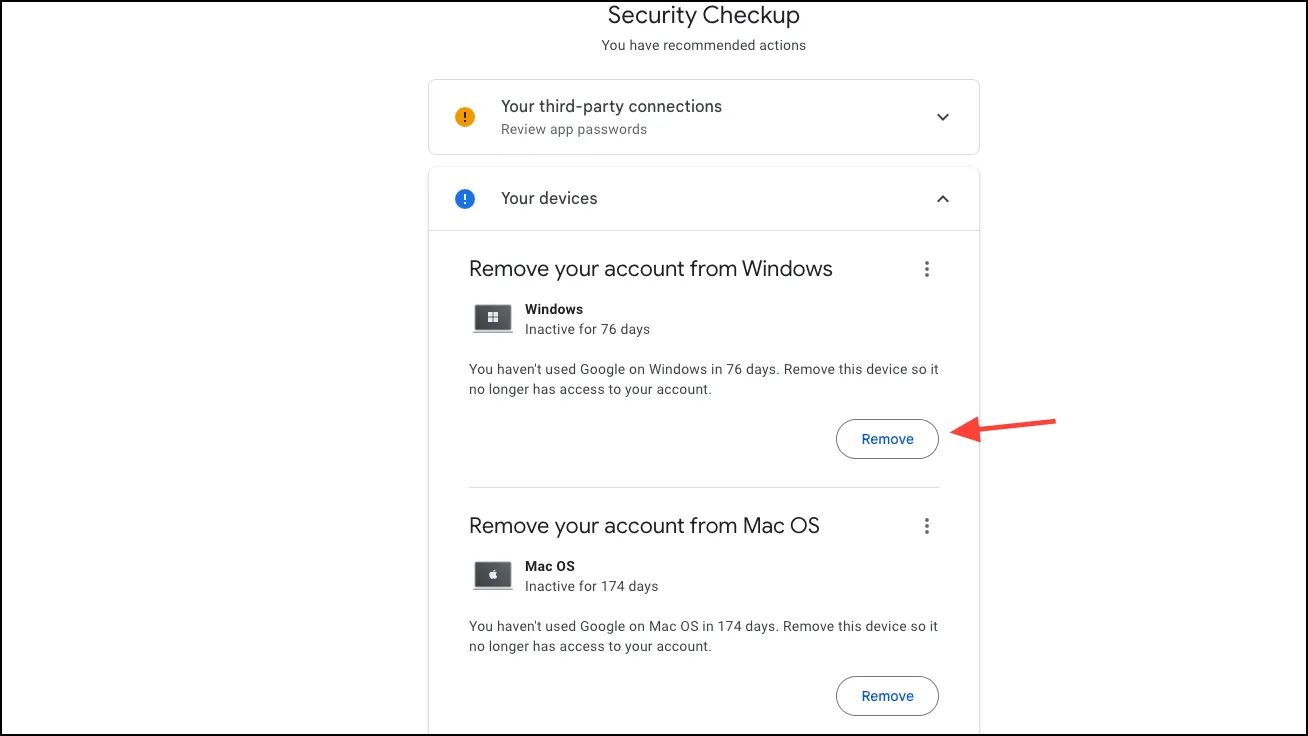
- Next, go to the page for managing your Google account.
- Click on ‘Security’ from the left side.
- Then, go to ‘Recent Security Activity’ and check that there’s no suspicious activity.
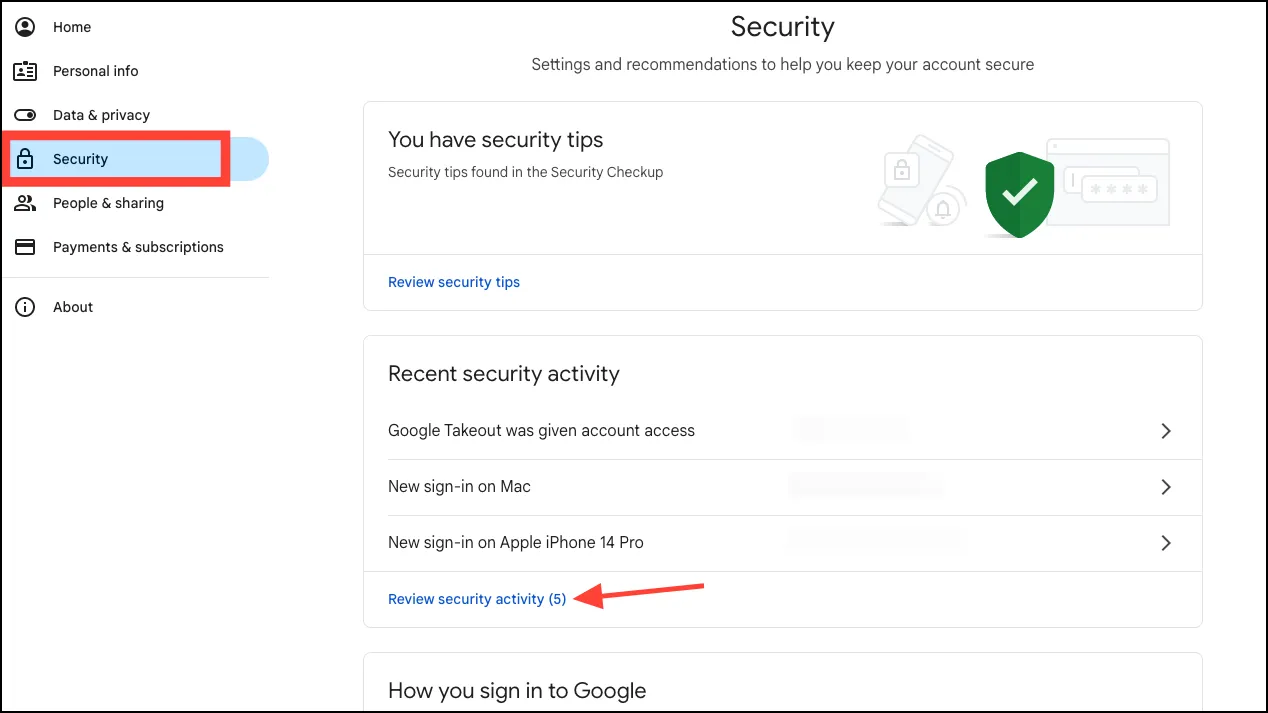
- If you see one you don’t recognize, click on it.
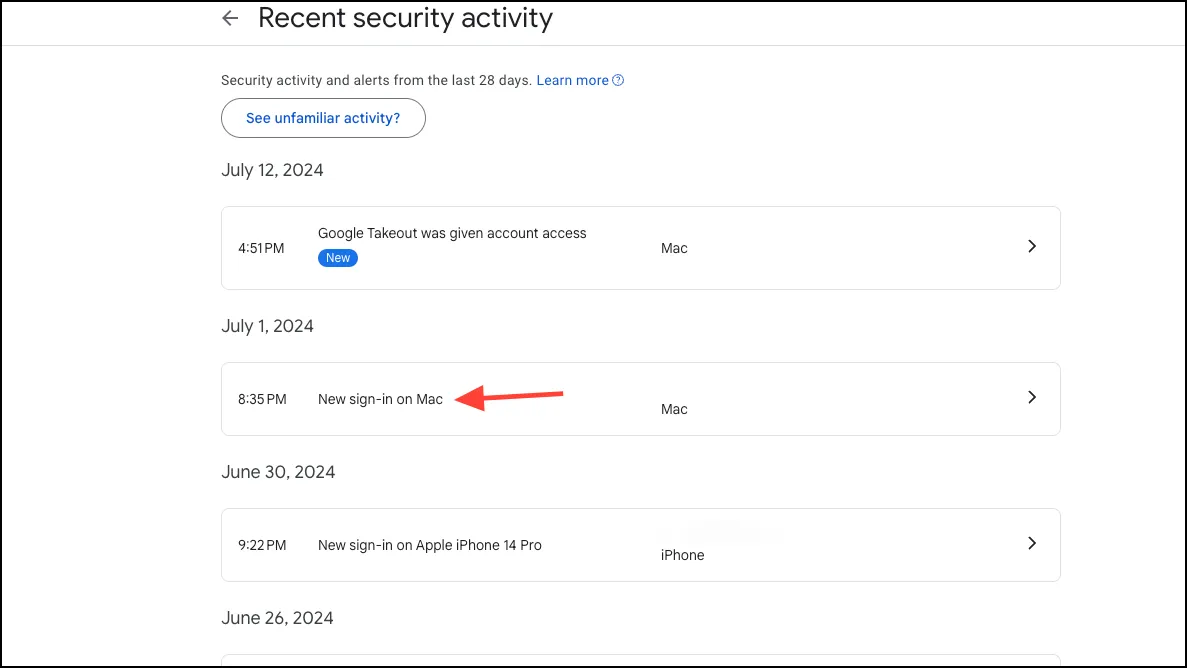
- Then, click on ‘No, secure account’ on the next screen.
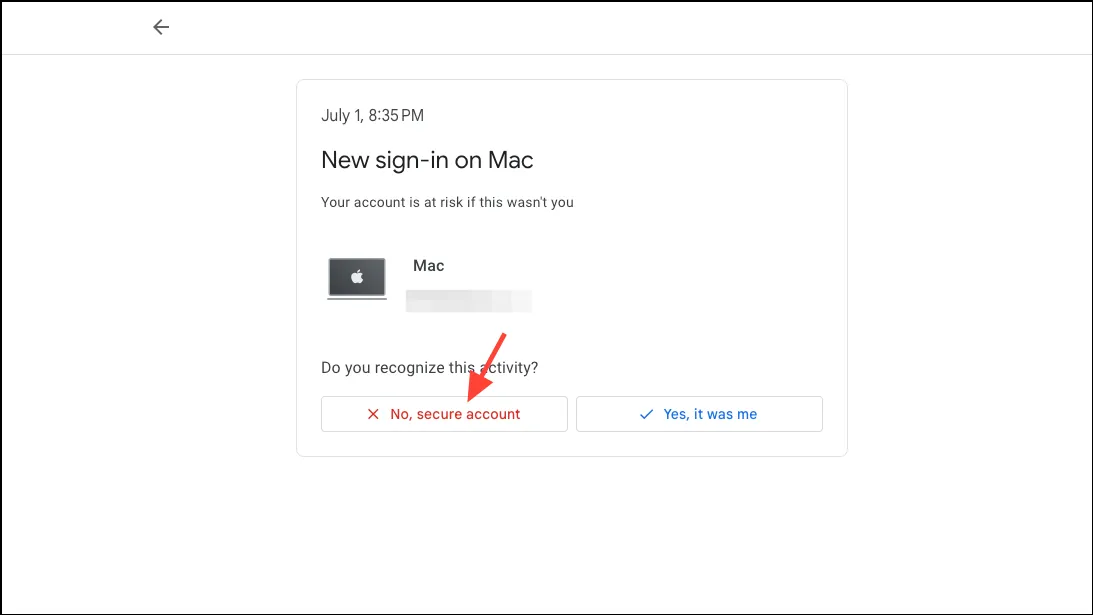
- Follow the steps on the screen. Depending on the activity, this might be something as simple as revoking a service’s access to your account or as drastic as changing your account password.
- When you change your password, you’ll be signed out of every location, except on the device you use to verify it’s you.
- You can also check the devices you can get the Google prompt on and your recovery phone numbers and emails from the Security settings to make sure that no one has altered that information.
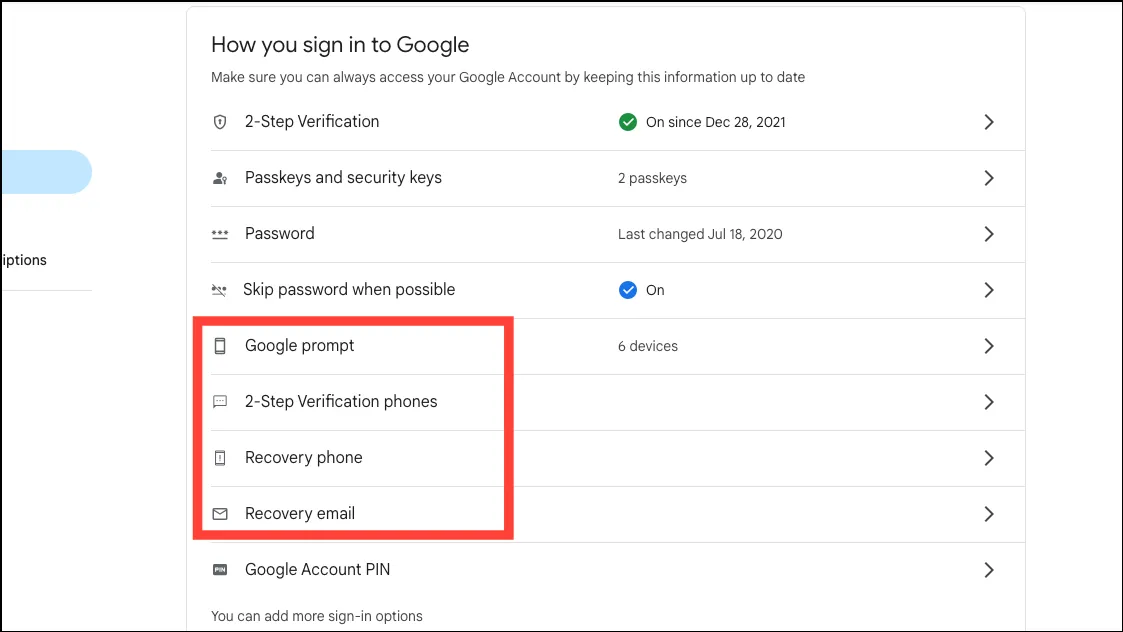
- If you can’t access your account in case someone has changed the password and recovery information, you’ll need to go to the account recovery page and answer the questions to recover your account.
Things to remember:
- If you have financial information saved in your Google account that has been compromised, for example, credit cards in Google Chrome or Google Pay, you should contact your bank and take the appropriate steps.
- If you also have other information or personal documents, like your passport, saved anywhere in your Google account such as Drive, Photos, etc., you should contact your local authorities and file a complaint.
- For users at higher risk of getting their accounts compromised, like journalists, politicians, human rights activists, etc., Google also offers an Advanced Protection Program that makes it difficult to get into someone’s accounts. While previously, it required the use of a hardware key, Google has now expanded the program to work with Passkeys as well so you don’t need to buy a hardware key if you don’t want to.
Apple ID
You can check whether your Apple ID is safe relatively easily using your iPhone, iPad, or Mac. You can also access this information by going to appleid.apple.com from a web browser.
- On your iPhone, iPad, or Mac, open the Settings app.
- Then, tap your name at the top on your iPhone/ iPad. On the Mac, click your name at the top of the left menu.
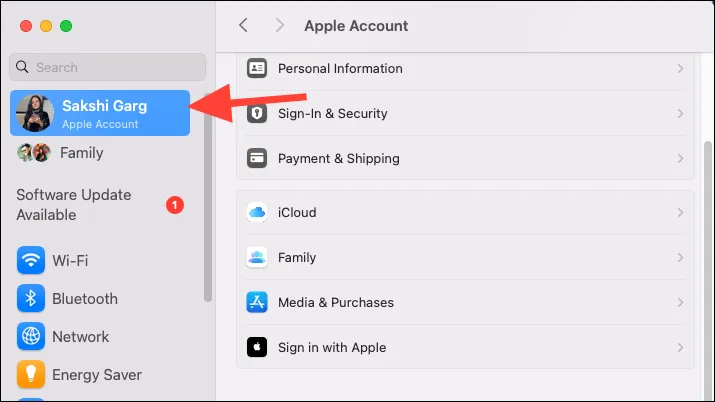
- Scroll down and you’ll be able to see a list of all the devices where your Apple ID is logged in.
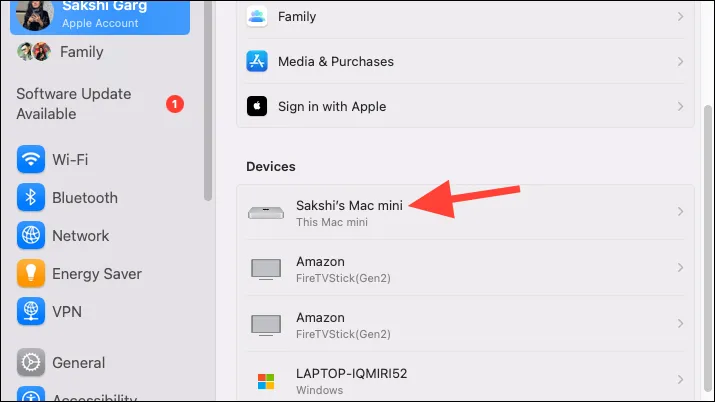
- You can tap on a device to see more information about it. If you don’t recognize a device, tap on ‘Remove from Account’.
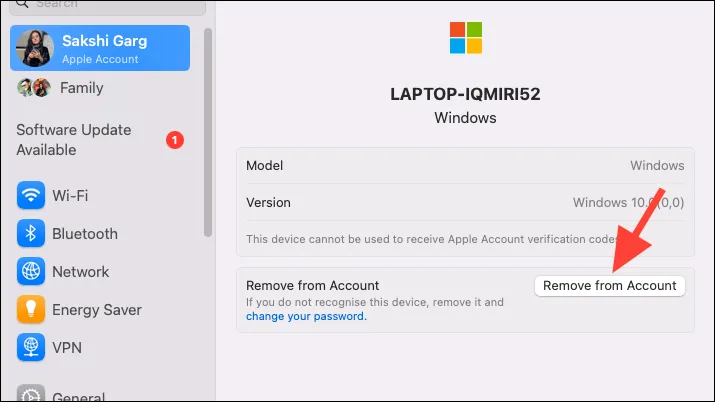
- You should also change your Apple ID password if an unrecognized device has access.
- If you can’t access your account and are unable to reset the password as well, you can start the recovery process for your Apple ID by going to iforgot.apple.com.
Things to remember:
- Set up two-factor authentication after securing your account if you haven’t already.
- If you’re using an email address from another provider with your Apple ID, say Google or Yahoo, make sure that that account is secure as well and only you have access to it.
Yahoo
Yahoo has similar tools to help you figure out where your account is active.
- Go to yahoo.com and sign in to your account.
- Hover over your profile picture and select ‘Overview’ from the menu to go to the account management screen.
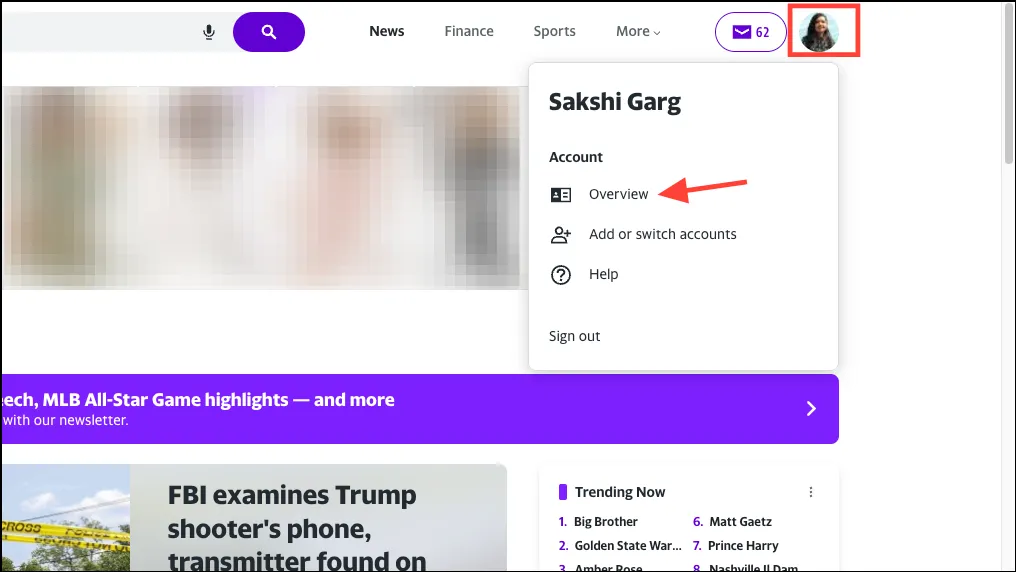
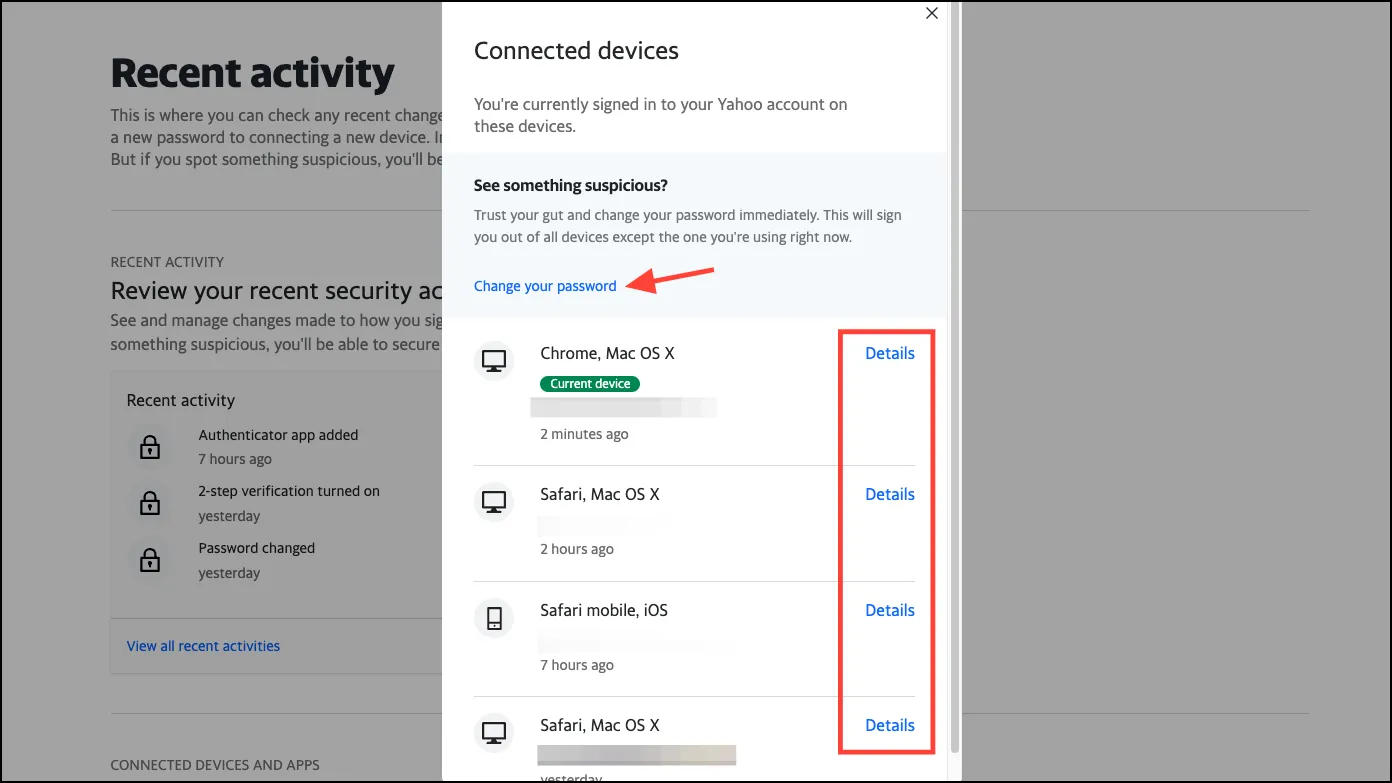
- Then, click on ‘View connected devices’ to see where your account is active.
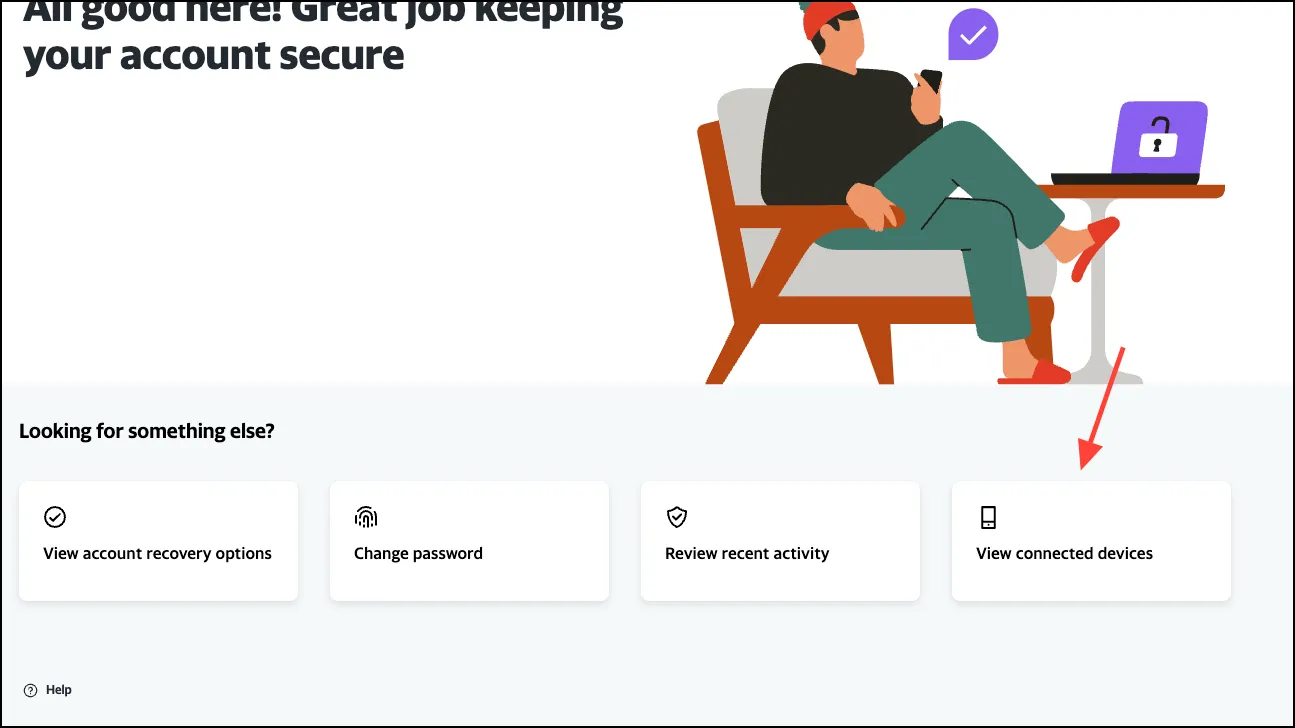
- Click on any activity you find suspicious to review it further. If you don’t recognize it, change your password. This will sign you out from all other devices except the one you’re using.
- From the account management page, you can also click on ‘Review Recent Activity’.
- This will show any activity related to your account, like changes in passwords, recovery phone numbers or emails, etc. If you find any suspicious activity here, change your password.
- Then, go to ‘Security’. Here, review and remove any unsanctioned recovery emails, phone numbers, or devices.
Microsoft
For your Microsoft or Outlook account, you can see your account activity by going to your account page.
- Go to microsoft.com and sign in to your account.
- Then, click on the Profile icon and go to ‘My Microsoft account’ from the menu.

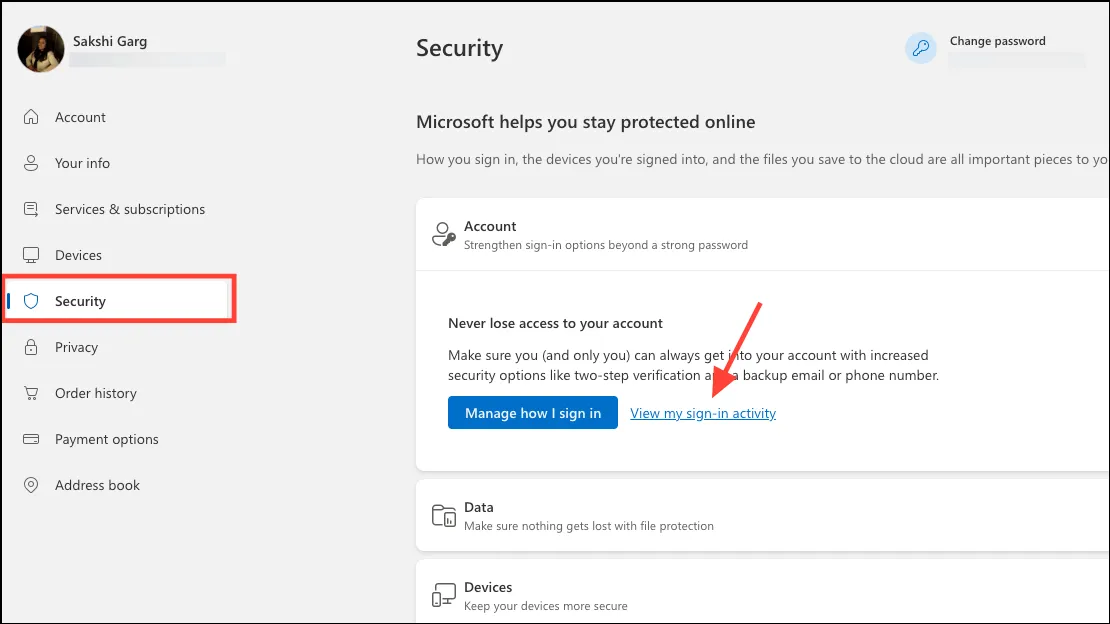
- Go to ‘Security’ from the left menu.
- Next, click on ‘View my sign-in activity’ under the ‘Manage how I sign in’ option.
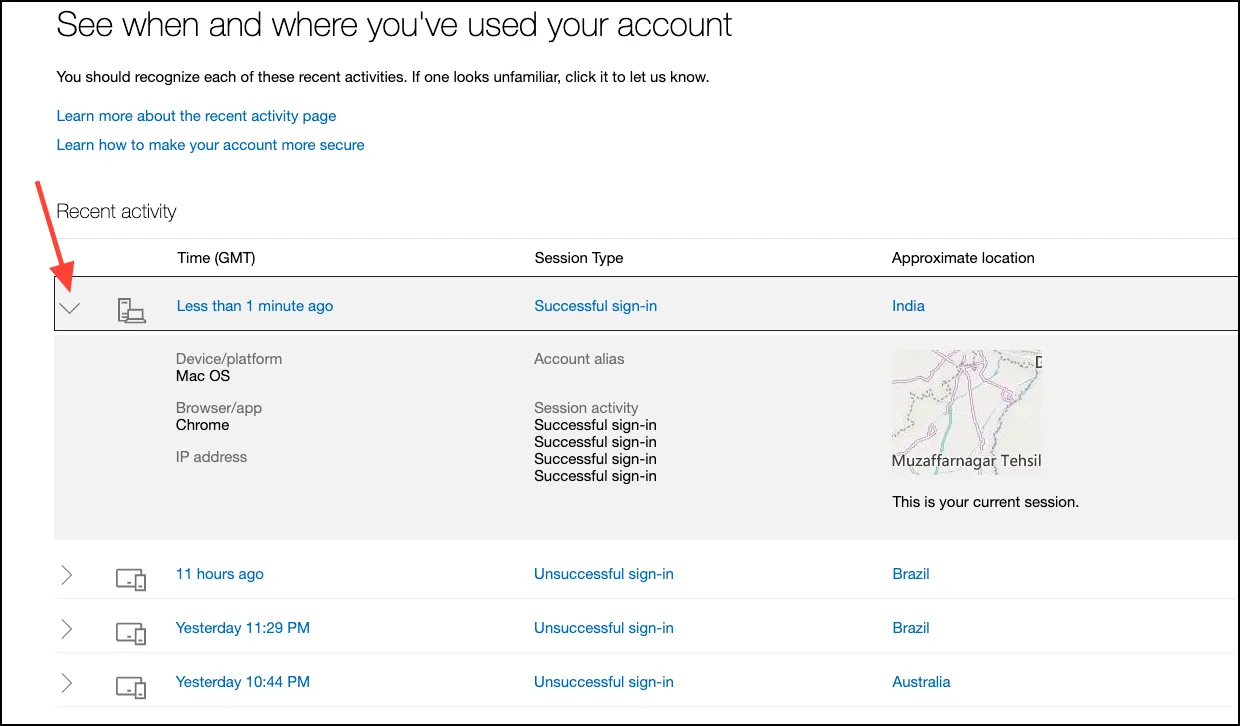
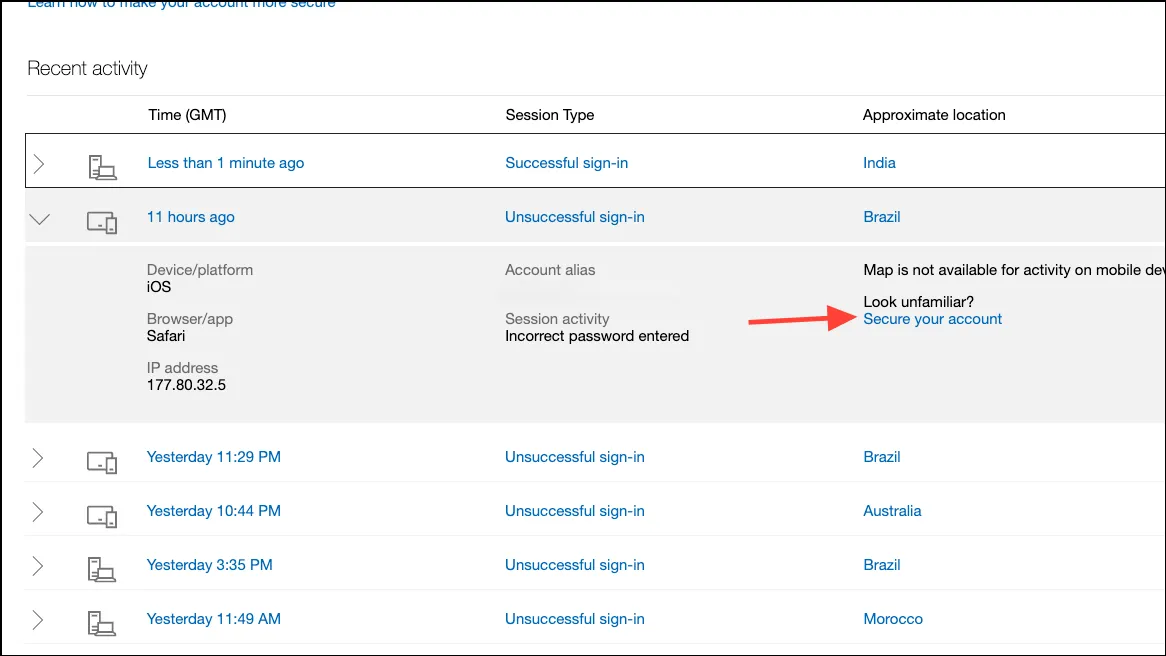
- Here, you can see all sign-in attempts (successful and unsuccessful) to your account.
- With every sign-in attempt, you can expand it to view more information like the device and browser used and the IP address.
- If you see any suspicious activity, click on ‘Secure your account’ to change your password.
Facebook and Instagram
Your social media accounts can also be hacked and result in disastrous consequences. Meta offers tools for its platforms so users can review their account activity.
- Open Facebook and go to
Settings and Privacy>Settings>Password and Security. - Then, click on ‘Password and Security’ once again.
- Next, click on ‘Where you’re logged in’ under Security checks to see your account activity.
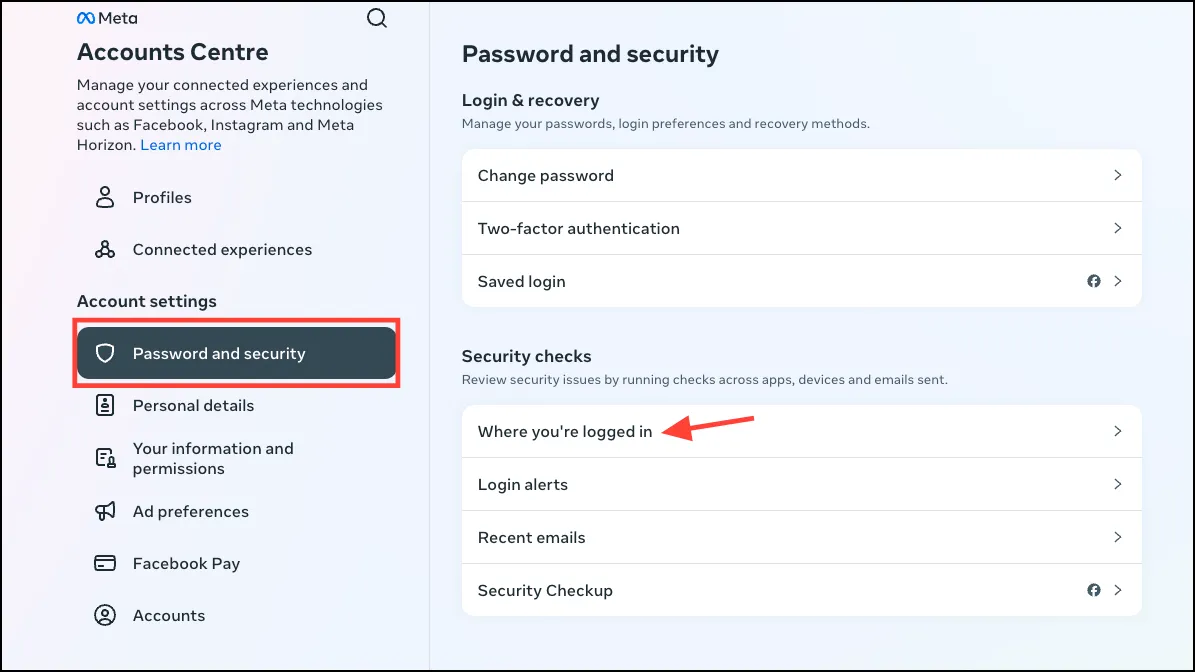
- If your Facebook account is connected to Instagram, you’ll be able to see the account activity for both platforms from here. Choose the platform you want to review the activity for.If your accounts are not connected or you don’t have a Facebook account, you can access the same page from the ‘Accounts Centre’ of Instagram settings as well.
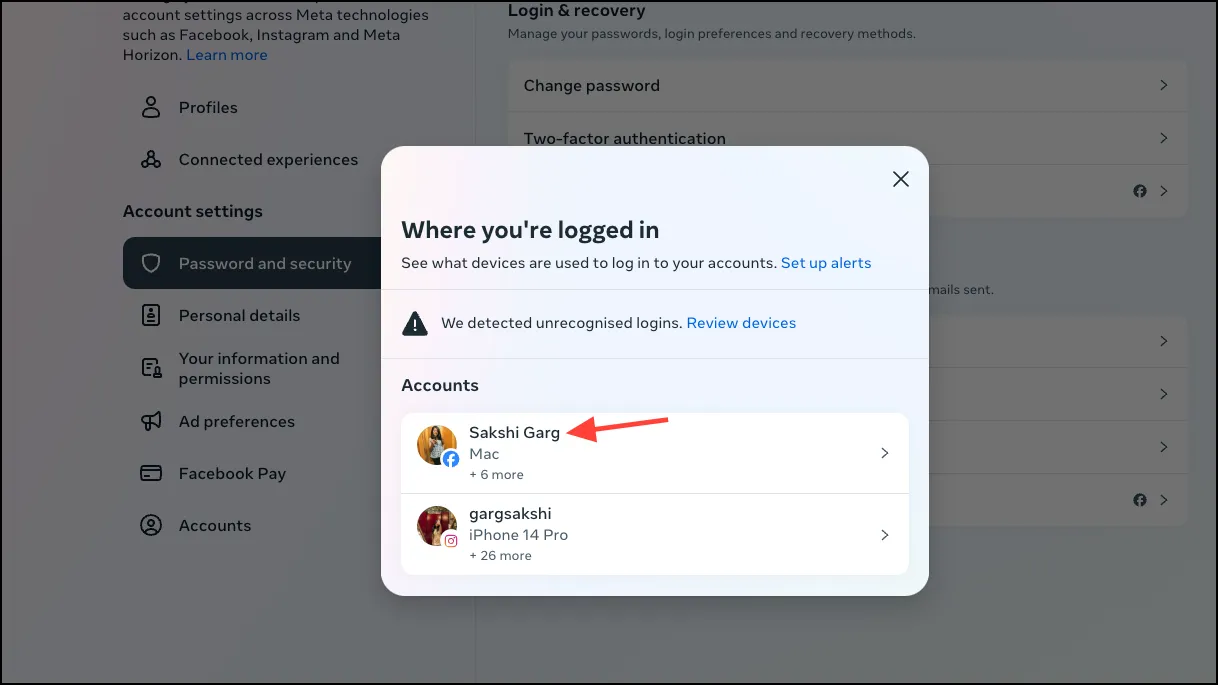
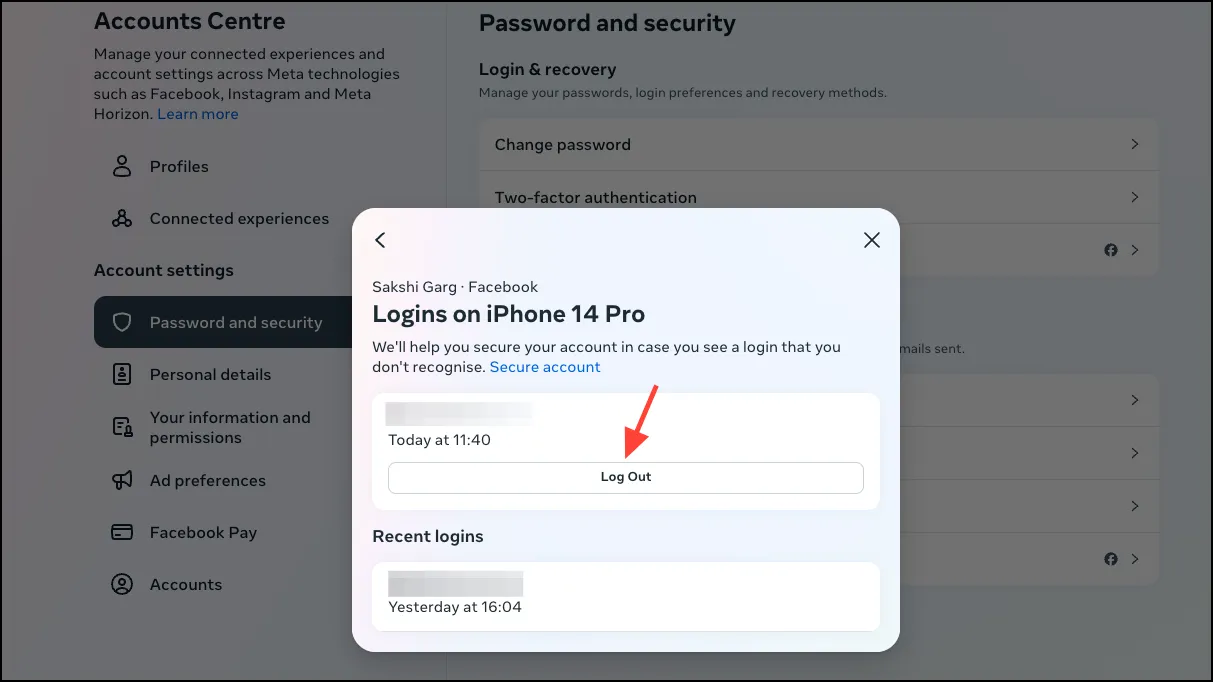
- Then, click on the device to further review it. You can see the device name, location, and time of the login. Click on ‘Log out’ to log your account out from a device you don’t recognize or no longer use. You can also set up alerts for when a device logs into your account.
Things to Know:
- Facebook and Instagram, like Google, offer Advanced Protection programs for both platforms for people whose accounts are more at risk of getting compromised. If you are a journalist, politician, or someone else in the public eye with a higher chance of getting hacked, you should enable Advances Protection which uses stricter measures at login.
It’s easy to know your account activity for WhatsApp, another Meta-owned platform.
- Open WhatsApp and go to ‘Settings’.
- Then, tap on ‘Linked devices’. On Android, tap on the ‘three-dot’ menu icon and then select ‘Linked Devices’ from the menu.
- You can view all the devices where your WhatsApp account is active.
- To remove a device, tap on it and select ‘Log Out’.
X (Formerly Twitter)
- To make sure that your X account isn’t being accessed by someone else, open the left menu and tap on ‘Settings and privacy’.
- Then, go to ‘Security and account access’.
- Next, go to the option for ‘Apps and sessions’.
- Here, you can see information for connected apps, sessions, account access history, and devices and apps where your account is currently logged in.
- If you go to ‘Sessions’, you can also log out of individual devices you don’t recognize or all other devices in one go.
- If you see any suspicious activity or devices, change your X password.
Tips for keeping your accounts secure
- Enable multi-factor authentication for your account.
- Use passkeys for accounts when they are available. Passkeys are more secure against phishing scams than passwords.
- Keep your recovery information updated to gain access to your account in case it is compromised.
- Scan your device for malware.
- Use hardware keys to protect your most sensitive accounts.
- If you’re a high risk individual, like a journalist or a human rights activist, contact professional services if you suspect your account has been compromised.



Deixe um comentário